Data leakage gives access to private data of SAP customers
— Note: the customer influence website is currently offline, the links in the post won’t work —
The SAP Customer Influence site exposes information about its users that goes beyond what the web site offers: a list of SAP customers, linked employees and their user ID and email address. That’s data for ~38.000 customers and ~120.000 users.
Personal data of SAP customers, partners and employees is leaked. The access is possible because the OData service that provides the data for the SAP Customer Influence (CI) site not only delivers the data you can see on the web page. It offers access to (almost) all information stored in SAP CI. As everyone can register for the site, personal data from SAP customers is available to everyone. Not even a hack is needed to gain access. Basic understanding of how OData works is enough. Calling the entity sets provides you with all data. The entities have a unique ID that is a simple number. Finding entries is therefore also possible by just counting up (100, 101, 102, …).
Attackers can use this information for social engineering attacks: Name, Email, User ID, last logon time, company, ideas allow for a sophisticated attack. Imagine the CI information combined with other available data on LinkedIn. With the email / user ID accounts can be blocked. As some accounts are a shared account for a customer center of excellence, it is possible to lock out a customer from SAP sites like support. Emails can be used to spam SAP customers. Assuming that the service is leaking this information since the start of CI, anyone can have obtained an impressive list of email address from the SAP universe.
Don’t confuse this with the actual design goal of CI. The CI site is designed to exposes selected personal data of every user that registered and used the site in the last 3 years. If a user is not active for more than 3 years, the personal data is GDPR-compliant deleted. As the Data privacy states:
- “Your name and company, and proposals and comments you make are visible to other registered users.”
- “User profiles provide the option to display personal information about you to other users, including but not limited to your name, photo, and basic information about your company”
While accessing information like companies and their employees is already accessible via the CI web site and aligned with the data privacy policy and terms of usage, the OData service exposes more data than you expect.
Exposing personal data that goes beyond this should not happen. The OData service is doing what is was designed for. The leakage might exist since the start of Customer Influence – or Idea Place as it was once known. As you do not need to hack CI, just call a service, it is possible that the extraction of emails and other information is already exploited since years.
SAP Customer Influence web site
Using only the CI website, the information you can see of other users is very limited. You see almost nothing, and that is how it should be and how it is described in the data privacy. Via the web site you only see basic information of other users: name, company, maybe a profile picture.
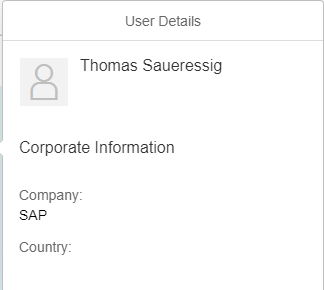
You cannot find out additional information about the company, or easily all the ideas a user contributed to. Any additional information like user ID, email or logon time is not accessible. The data privacy explicitly states that you must be careful what you post: “You should therefore not include any Personal Data of yourself and must not include any Personal Data of others in such proposals or comments”. Linking users to company is in theory possible via the web site, albeit in a very time-consuming way. You’d have to go through either all users or all ideas manually.
OData service
The OData service however gives access to so much more. The CI powering OData service throws the information literally at you. It is a good example of what can go wrong when designing an OData service. I think I will write a follow up post about this.
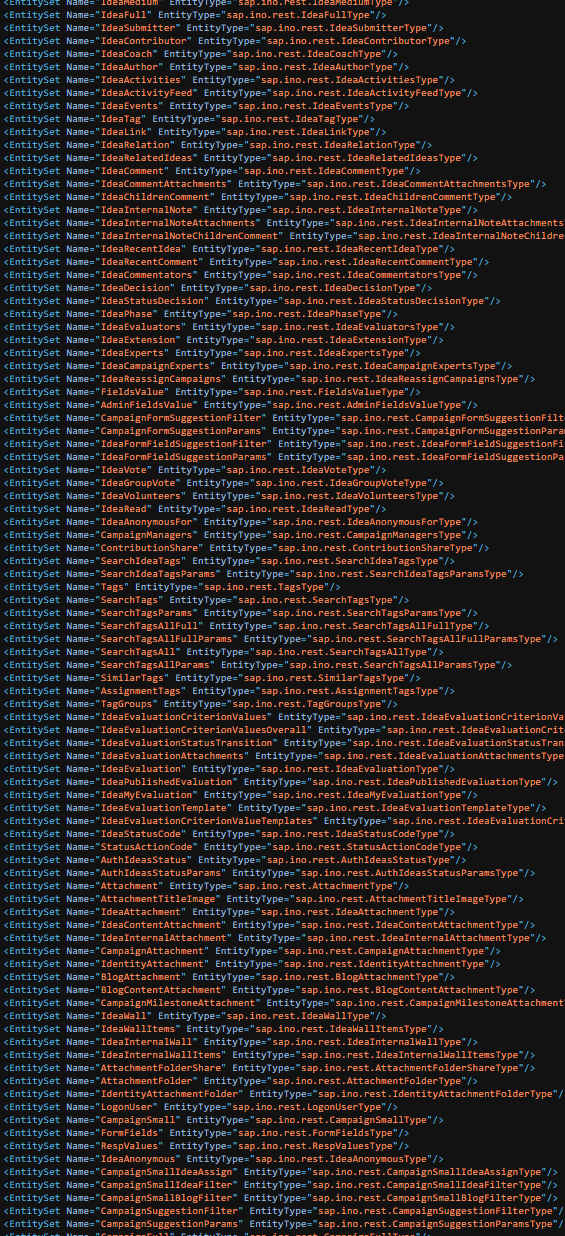
There are entities for groups, group members or identities (don’t click these, your browser tab might crash). Giving access to companies, their employees and detailed user information. The service is not enforcing any kind of restrictions. It gives access to the whole list of entity sets and data. Allowing access to all information available by the service. No direct access to an entity needed or searching. It’s like a database dump. The service is not using pagination or any other way to limit the consumption. Given a good enough REST client, the service simply throws data at you: get all groups, users or ideas? It delivers dozens of megabyte, if not hundreds. It is a database dump.
Try it out
(Note: I am not sure if this will allow SAP to block you from accessing CI via its TOU)
You need to have a valid SAP Customer Influence user. There is no way to do this anonymously. You are going to query an OData service, using standard functionality provided by GetEntitiySet and GetEntity. Requests may be logged and traced back to your user.
Curious what the service exposes? Want to try it out? Want to know if you are affected and what information about you or your company is available? All you need is an SAP Customer Influence user. Access to CI you get for free from SAP. For registration you do not need to be an SAP customer. After logging on to the CI site you can start using the OData service.
Not using the service is not possible, the web site relies on it to receive data. Open the browser network trace and you can see that the service is called by the web site. The service is there, it is used by the web site, and honestly: if there are no actions taken to ensure that the service is not exposing data you should not see, then it works as designed. Just don’t use the data for creating a sales proposals or spam or …
How do you use the service? It gets a little bit technical, but I included samples.
Search for a company
You can search for companies (or just call entity set groups and get all companies available. Yes. all at once. No pagination. Not even an empty set to force you to search for a given company. Currently there are 38.500+ available). A group / company is based on the domain name. Maybe the one you are working for is included. To get a list of all groups whose name end on sap.com:
https://influence.sap.com/sap/ino/xs/rest/community/odata.xsodata/Groups?$filter=substringof(‘sap.com’,GROUP_NAME)
In the search results you get an entry for SAP:
https://influence.sap.com:443/sap/ino/xs/rest/community/odata.xsodata/Groups(GROUP_ID=5,GROUP_NAME=’sap.com’)
And you can see all members of that group (aka employees):
https://influence.sap.com/sap/ino/xs/rest/community/odata.xsodata/Groups(GROUP_ID=5,GROUP_NAME=’sap.com’)/Members
You can get the same information for any other company available in CI. Just replace sap.com in the filter with e.g. your own company and from there you can see the linked employees. The company here is deducted from the email, so if your email address is <name>@<domain>.<tld>, then you can search for <domain>.<tld>.
Retrieve user details
There are more than 27.000 entries for SAP employees, your browser might take some time to load them correctly. Some are duplicate, the unique number of entries is a lower. You can filter for CI users via OData, e.g., for user name and/or group. I’ll use the name of an SAP employee whose data you can google and that has an CI account: Thomas Saueressig.
Let’s first see what the CI web site is offering. Searching via the web site triggers a request to the OData service:
SearchIdentity(searchToken=’thomas%20saueressig’)/Results?$skip=0&$top=20&$orderby=NAME%20asc&$filter=TYPE_CODE%20eq%20%27USER%27
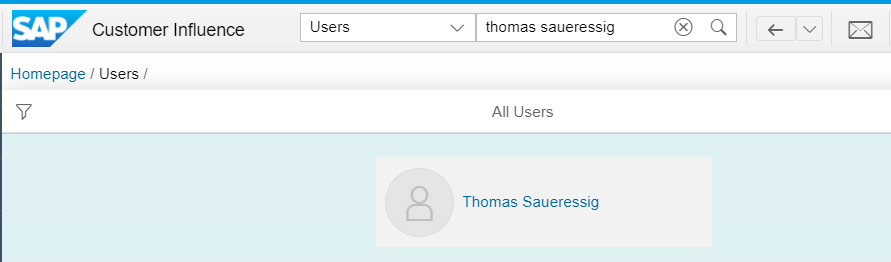
Information not needed is returned, including the user ID.
"ID": 197400, "NAME": "Thomas Saueressig", "USER_NAME": "D04---7",
This is interesting, as only the ID is used to retrieve the user information going to be shown to the user. And that call returns only what you should see.
https://influence.sap.com/sap/ino/xs/rest/common/identity_profile.xsjs/?USER_ID=197400
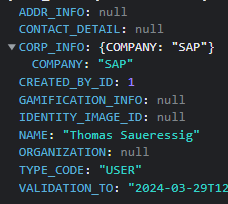
The OData service however returns also the email everything. Now the service starts getting interesting. Data privacy states that the email is only shared in specific use cases with other users, like an event or seminar. To quote data privacy: “If you register for an event, seminar, or webinar of SAP, SAP may share basic participant information (your name, company, and email address) with other participants of the same event, seminar, or webinar for the purpose of communication and the exchange of ideas.” Let me add to that statement: OR you simply call the OData service. Why is the service at all returning this information?
https://influence.sap.com/sap/ino/xs/rest/community/odata.xsodata/GroupMembers?$filter=substringof(%27Thomas%20Saueressig%27,MEMBER_NAME)%20and%20substringof(%27sap.com%27,%20GROUP_NAME)
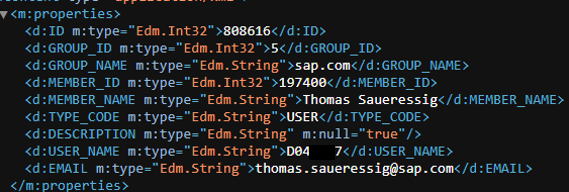
To get more detailed information, the provided MEMBER_ID value can be used to gain additional insights about a user: company information.
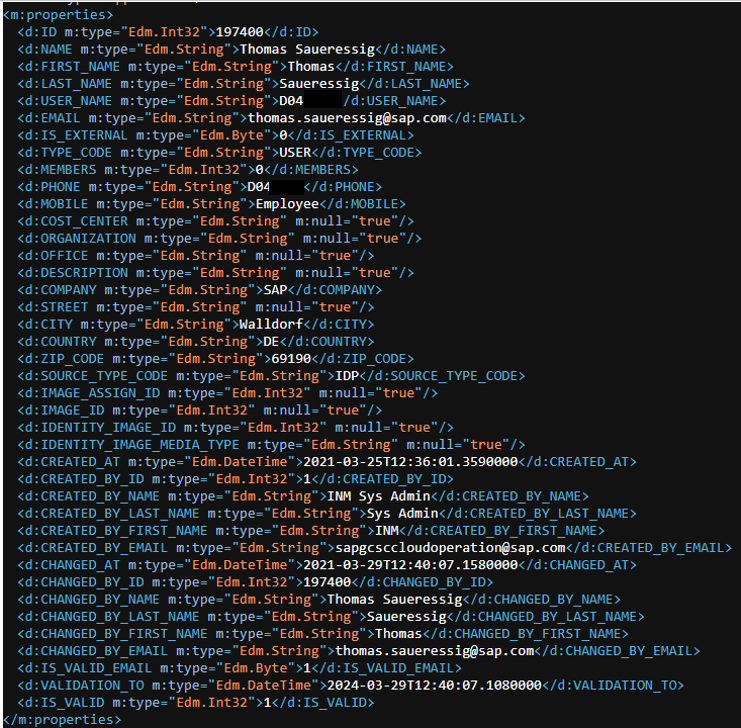
The service provides additional information like:
- Company
- User ID
- If the Email is validated
- Last logon time to CI by user
You can search for properties too. If you want to know who works for a company that is based on a specific country, you can do so: just create a filter and inform the country code:
https://influence.sap.com/sap/ino/xs/rest/community/odata.xsodata/LeanIdentity?$filter=COUNTRY%20eq%20%27RU%27
Same works for company name:
https://influence.sap.com/sap/ino/xs/rest/community/odata.xsodata/LeanIdentity?$filter=COMPANY eq ‘Gazprom’ (link won’t work, you’ll have to figure out a correct company name by your own)
The service provides this for every registered customer and user in the system. Best about the OData service: You do not even have to search! The OData service throws the data at you. The entity sets are all giving complete access, and are not even using pagination or UUIDs. If you call the Groups entity, the answer is a 15 MB file containing all CI groups. GroupMembers? Breath taking 250MB. Identities? 200MB. I’ll call the data leakage by the OData service from now on: SAP/4HACK.
How bad is this?
Why did I named this post data leakage? The OData service shares more data than needed. Actions to prevent pulling out massive amount of data are not in place. Therefore the OData service leaks CI data.
Passwords are not exposed, and you cannot use CI to log in as another user. So, it is not super bad. If it’s OK depends on how you feel about seeing your email and user ID exposed to thousands of CI users. As everyone can sign up, in theory your email and user id is exposed to everyone. The current security and data protection measurements can be summed up as: I do not see you, so you cannot see me. Just because the CI web site is not showing the information does not mean it is not delivered and not available.
You can get a list of SAP customers (companies). Of course, it is not a list of all customers, only the ones using CI. If you want to know if a company is an SAP customer you can also consult their job site. Via the Members link you get a list of employees that is using CI. So far, this information you might get from LinkedIn or from the normal CI web site search. That the OData service makes it so easy to get this information can be questioned. The information can be used by attackers for social engineering. Colleagues can be found out through the groups entity. This can be used to create spam emails that include valid information like your last submitted idea, comment, or logon time. Your SAP account can be blocked. Whole teams can be locked out of SAP when they use a shared account (e.g. COE).
I do not know since when the OData service shares willingly the information. Maybe since the start of CI years ago. When you wonder why entities are named idea and not influence: IdeaPlace is the old name. What makes me also wonder is that the Lean Identity entity includes properties for phone and mobile. These are overwritten with values. What are the changes that the service already delivered these information’s in a previous version? And why include a property cost center?
The OData service informs me that there are close to 23.000 SAP employees listed. In total it is over 120.000 users. Some might duplicate as they might have left or switched companies in the last 3 years. Even so, the overall list of user IDs and email addresses is impressive.
So, how bad is it? I think it is bad. Specially as the leakage can be stopped by simple actions like good OData design.
Actions
I do not know what SAP is going to do. I’d like to see the following
- Ensure that the service is not sending out private data to any registered user. I do not see the need to send out ID (web) and email (OData) when this information is not even used on the web site.
- Consider taking the SAP CI site offline to fix the service.
- If you are CI user and surprised that your email and user ID is made available as shown above, you can report it: send an email to poststelle@lfdi.bwl.de.
- Send an email to every registered user of CI and inform them what happened. I talked with a few people, no one was happy that their user ID is accessible.
Reported
And yes, for those wondering: I reported this to SAP. I reported it via back channel, via official channel. I informed that I am going to write a post about this. The answer I got: works as designed. And silence. In my opinion, SAP should have taken some actions already, like informing CI users that personal data is accessible and adjust the OData service. They had time to do so. As this did not happen, I understand it as: the service is working as intended and everything is alright. Therefore: calling a service with my user should only return data I have the right to see, and judging from SAP’s response, this is what the CI service does.
As it seems to be alright, sharing how to get access to data via the OData service should also not be a problem. Again: this is not a hack. You do not need to attack the service. It is just interacting with an OData service and doing for what OData was designed. Remember: whatever you find, do not share it with others.
Password reset
If you wonder how the user ID or email can be used to lock out a user. Knowing the user ID or email address allows to block a user via SAP’s public IdP (accounts.sap.com). It blocks a user after 5 failed login attempts for 1 hour. If a user needs to e.g. log on to BTP cockpit with the universal ID account. Or to the SAP Support launchpad: not possible. This can cause quite some problems. Make sure to not share your user ID or email address on the internet!
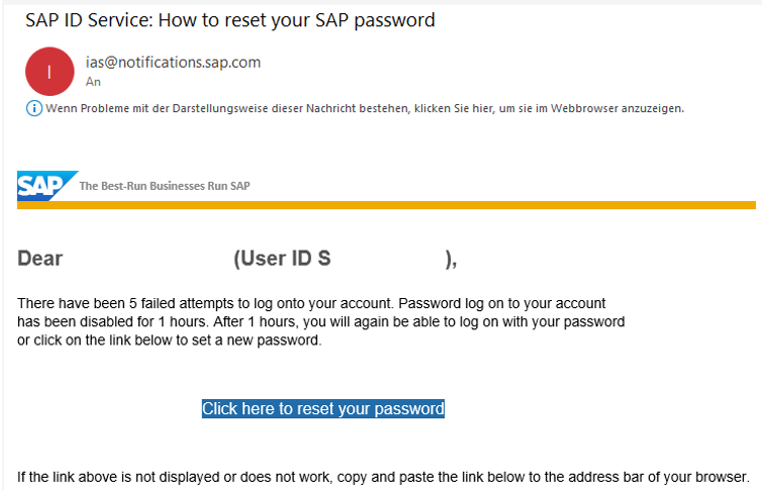
This is how other sites and IDPs work too. The only problem is to find out a list of valid IDs. As CI exposes thousands of email addresses, a script kid can cause severe problems.
16 Comments
Martin English · March 19, 2022 at 08:27
While you correctly state that the password, for example, is not shared, the fact you can use the S number to lock users is bad enough.
Apart from that (and I’m not a GDPR expert), is this actually GDPR compliant ? ie, the collection and dissemination of unnecessary day ?
HTH
Tobias Hofmann · March 19, 2022 at 10:32
Well … to quote myself “I think it is bad”
S-User ID is easily guessable, it gets interesting when you can link it to a company, and even more interesting when you can than link it to a user.
I heard of a few companies that are requesting new S-Users. To access SAP BTP Cockpit an S-User is needed, blocking a company to access the cockpit might be something you do not want – as the affected company. And GDPR? Well, if it is a violation, SAP needs to inform the CI users, which did not happen yet.
Additional SAP Customer Influence platform findings | It's full of stars! · March 16, 2022 at 16:30
[…] I looked at the SAP Customer Influence website. Besides an interesting OData service I came across several other points I think are worth […]
Customer data leaking via SAP community site - DUK News · March 18, 2022 at 12:55
[…] and comments, those with knowledge of SAP’s back-end can easily get hold of more information, argues SAP consultant Tobias Hofmann in his […]
Customer data leaking via SAP community site - Times News UK · March 18, 2022 at 13:09
[…] and comments, those with knowledge of SAP’s back-end can easily get hold of more information, argues SAP consultant Tobias Hofmann in his […]
SAP community website leaks member data to savvy users – Best Soundcloud Rappers 2019 · March 18, 2022 at 13:31
[…] and comments, those with knowledge of SAP’s back-end can easily get hold of more information, argues SAP consultant Tobias Hofmann in his […]
SAP community website leaks member data to savvy users - CyberGen · March 18, 2022 at 17:42
[…] and comments, those with knowledge of SAP’s back-end can easily get hold of more information, argues SAP consultant Tobias Hofmann in his […]
Customer data leaking via SAP community site - Cybersecureness · March 18, 2022 at 18:18
[…] and comments, those with knowledge of SAP’s back-end can easily get hold of more information, argues SAP consultant Tobias Hofmann in his […]
Buyer information leaking by way of SAP group website - news@enetworklink · March 19, 2022 at 06:56
[…] and feedback, these with data of SAP’s back-end can simply pay money for extra info, argues SAP consultant Tobias Hofmann in his […]
SAP Community Website Leaks Member Data To Savvy Users - ThreatsHub Cybersecurity News · March 19, 2022 at 16:37
[…] and comments, those with knowledge of SAP’s back-end can easily get hold of more information, argues SAP consultant Tobias Hofmann in his […]
Customer data leaking via SAP community site • The Register | News Dome · March 20, 2022 at 07:26
[…] and comments, those with knowledge of SAP’s back-end can easily get hold of more information, argues SAP consultant Tobias Hofmann in his […]
SAP community website leaks member data to savvy users - Science News · March 20, 2022 at 12:29
[…] and comments, those with knowledge of SAP’s back-end can easily get hold of more information, argues SAP consultant Tobias Hofmann in his […]
SAP community website leaks member data to savvy users - News around the world · March 20, 2022 at 12:56
[…] and comments, those with knowledge of SAP’s back-end can easily get hold of more information, argues SAP consultant Tobias Hofmann in his […]
Buyer knowledge leaking through SAP group web site • The Register – Blastace · March 20, 2022 at 22:51
[…] and feedback, these with data of SAP’s back-end can simply pay money for extra data, argues SAP guide Tobias Hofmann in his […]
Mind the protocol | It's full of stars! · May 23, 2022 at 10:30
[…] IDs. The user ID of the owner of the document (create, update) are accessible. With the data exposed from the customer influence, an attacker might be able to combine that information (name, company, customer influence idea, […]
Data pelanggan bocor melalui situs komunitas SAP • The Register – Tech Online · February 8, 2023 at 23:55
[…] memiliki pengetahuan tentang back-end SAP dapat dengan mudah mendapatkan lebih banyak informasi, bantah konsultan SAP Tobias Hofmann di […]