Install a server certificate in SAP NetWeaver ABAP – 3.1 Create a SSL/TLS Server PSE
SAP stores certificates in PSE files (for the Java guys: JKS). By default, there are several PSEs available, one for each use case (system, SSL, web service, etc). A PSE has a subject which stands for the name of the server. Changes are good that the subject value created by SAP does not match your reality. The following steps show how to create a PSE for your SSL server. SAP Help
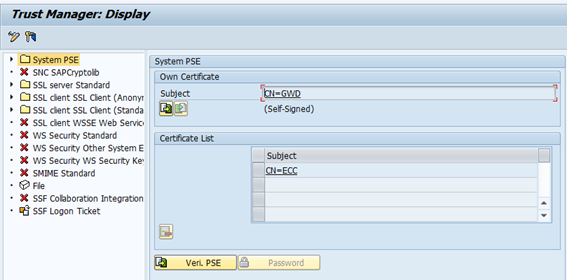
Transaction: STRUST
Change into edit mode:
Select the SSL Server PSE:
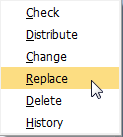
Right click to open the context menu and select replace
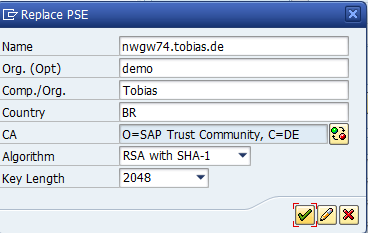
Give information about the new PSE. This creates a private and public key for the server CN informed for this PSE. The key will be automatically self-signed, but as the PSE contains the private key, it is no problem to create a certificate request and get the certificate signed by a CA.
The data informed here MUST match the data of the HTTPS server. The name field is the CN of the certificate; therefore this field MUST be the same as the FQDN of the server. That is, when the server is accessed by browsers as https://nwgw74.tobias.de, the field MUST be nwgw74.tobias.de.
Click OK
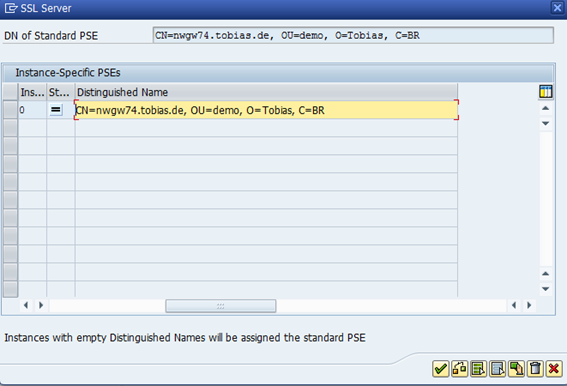
Confirm the information. Make sure the CN name is correct. This changes the PSE for SSL Server.
You now have a PSE with a private and public key for the CN nwgw74.tobias.de. This certificate is self-signed. While you can now access ICF via HTTPS, each and every browser will give you a warning message that the certificate used is not trustworthy. To change that, a CSR must be created and signed by a CA.
Result
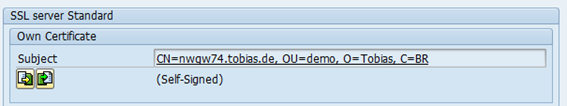
You now have a PSE for the server nwgw74.tobias.de with a private key and a self-signed certificate.
2 Comments
tim · May 2, 2021 at 17:54
Hallo Tobias,
Ich habe in STRUST / Server PSE ein Key Paar erstellt. Wie kann ich ohne eine Zertifizierungsstelle, das Server Zertifikat signieren, damit im Browser kein Zertifikatsfehler kommt ?
Geht es überhaupt ohne einer Zertifizierungsstelle ?
Danke
Tobias Hofmann · May 3, 2021 at 21:13
Hallo Tim,
Das Zertifikat wird so lange vom Browser als ungültig angesehen, bis der Browser dem Zertifikat vertraut. Es muss also in der Vertrauenskette des Browsers sein. Das hängt vom Browser ab. Bei Chrome im Mac kann man das Zertifikat in den Schlüsselbund importieren, dann dort als Vertrauenswürdig aktivieren und dann nimmt Chrome es an. Bei Firefox geht das glaube ich direkt in Firefox. Bei anderen Browsers kann es auch die CA Konfiguration des Systems sein.