OCSP part 4 – Configure CA to support OCSP Responders
After having the OCSP service installed and configured, the CA must be made aware of the service. Only after this, new emitted certificates by the CA will include the OCSP information. This means that you can run a OCSP service without having it included in the client certificates. In that case, clients can be configured to use a static OCSP address to validate the status of the certificate, while other clients won`t be able to do this.
To configure a CA to support an Online Responder or OCSP responder services
-
Open the Certification Authority snap-in.
-
Open the properties of the CA.
-
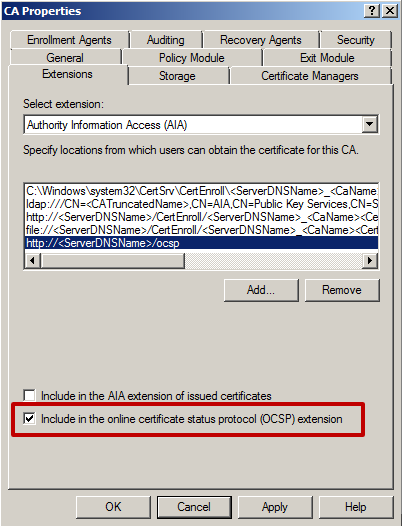
Open the extensions tab. By default, the CRL distribution point (CDP) list is shown.
-
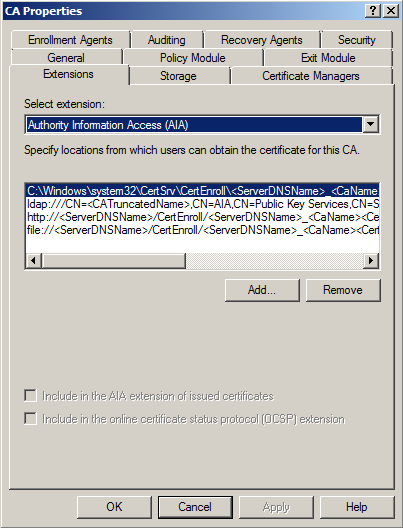
Change from CDP to Authority Information Access (AIA)
-
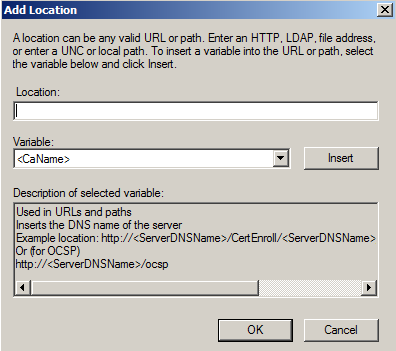
Click on Add to add a new location.
-
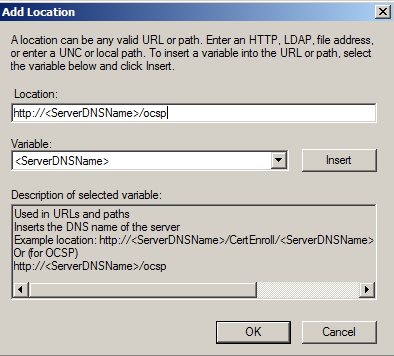
Specify the locations from which users can obtain certificate revocation data. This is the URL under which the OCSP service is installed.Make sure that the clients can resolve the DNS name and communicate with the service.
Example: http://<ServerDNSName>/ocsp
-
Select “Include in the online certificate status protocol (OCSP) extension”. This makes the OCSP URL available in the certificate.
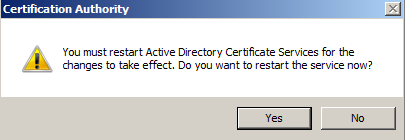
You will have to restart the CA service to make the new configuration effective.
-
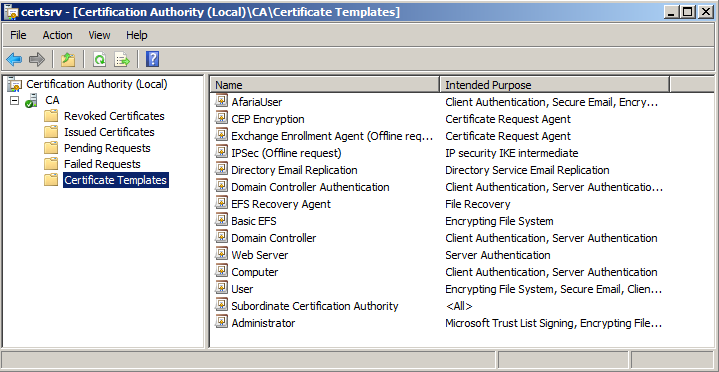
Next, you will have to include the OCSP certificate in the list of available certificates of the CA.
-
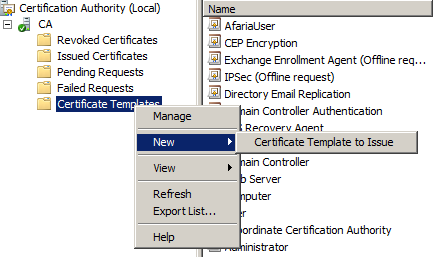
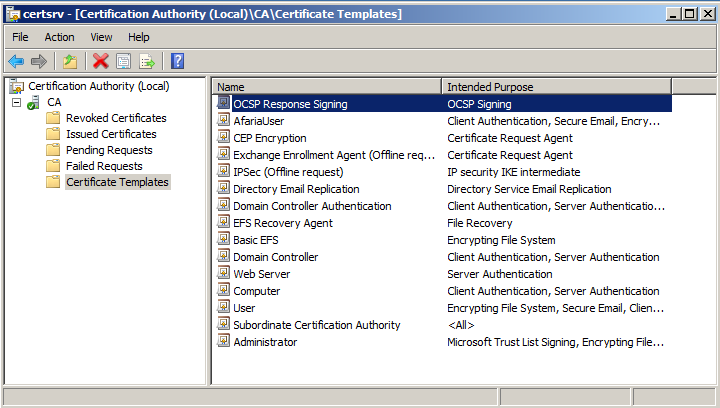
Open the CA snap-in, select Certificate Templates, right click and choose “New Certificate Template to Issue”
-
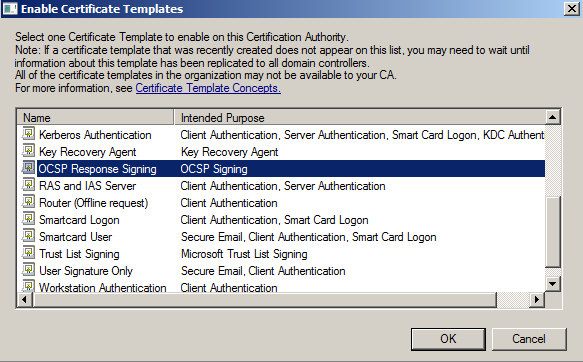
Select the OCSP Response Signing certificate.
-
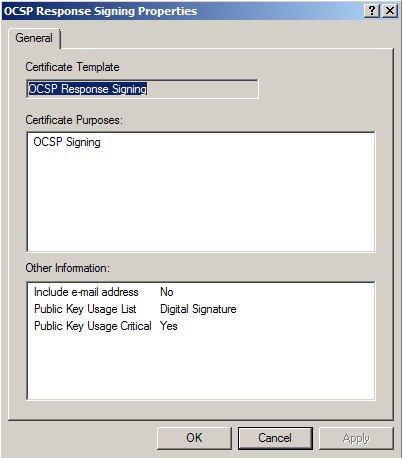
To check that it worked, select the certificate and open its properties.
1 Comment
Online Certificate Status Protocol | It`s full of stars! · August 30, 2016 at 09:23
[…] OCSP part 4 – Configure CA to support OCSP Responders […]