OpenSSL CA to sign CSR with SHA256 – Sign CSR issued with SHA-1
The overall process is:
- Create CA
- Private CA key
- Create private key
- Check private key
- Public CA certificate
- Create public certificate
- Check public certificate
- Private CA key
- Sign CSR
- SHA-1
- Create CSR using SHA-1
- Check CSR
- Sign CSR enforcing SHA-256
- Check signed certificate
- SHA-256
- Create CSR using SHA-256
- Check CSR
- Sign CSR
- Check signed certificate
- SHA-1
Sign CSR request – SHA-1
When a CSR is created, a signature algorithm is used. Normally, this is SHA-1. Installing a TLS certificate that is using SHA-1 will give some problems, as SHA-1 is not considered secure enough by Google, Mozilla, and other vendors. Therefore, the final certificate needs to be signed using SHA-256. In case the CSR is only available with SHA-1, the CA can be used to sign CSR requests and enforce a different algorithm.
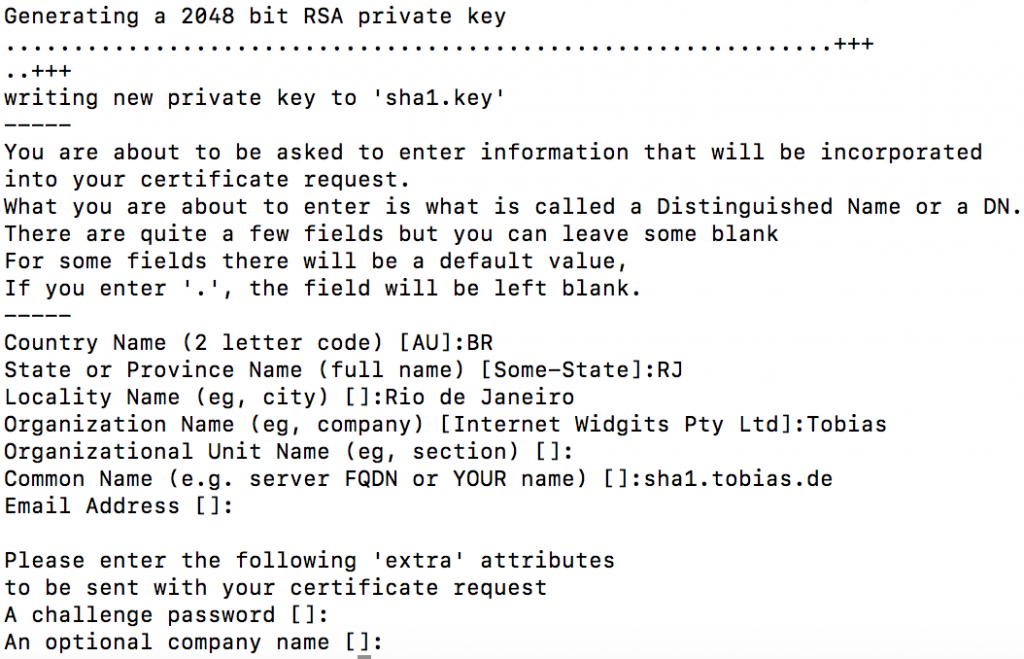
Create CSR using SHA-1
openssl req -out sha1.csr -new -newkey rsa:2048 -nodes -keyout sha1.key
The command creates two files: sha1.key containing the private key and sha1.csr containing the certificate request.
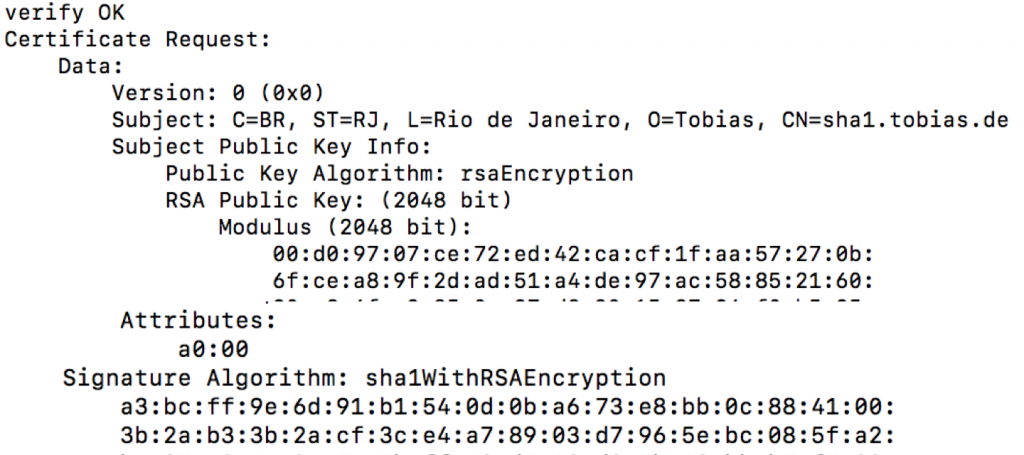
Check CSR
openssl req -verify -in sha1.csr -text -noout
The signature algorithm of the CSR is SHA-1
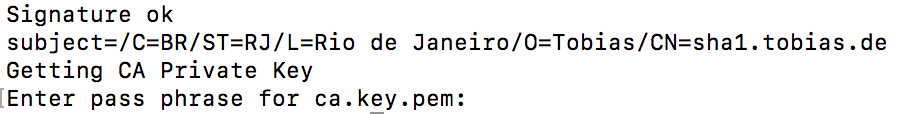
Sign CSR enforcing SHA-256
Singing the CSR using the CA
openssl x509 -req -days 360 -in sha1.csr -CA ca.cert.pem -CAkey ca.key.pem -CAcreateserial -out sha1.crt -sha256
This will sign the CSR using SHA-256.
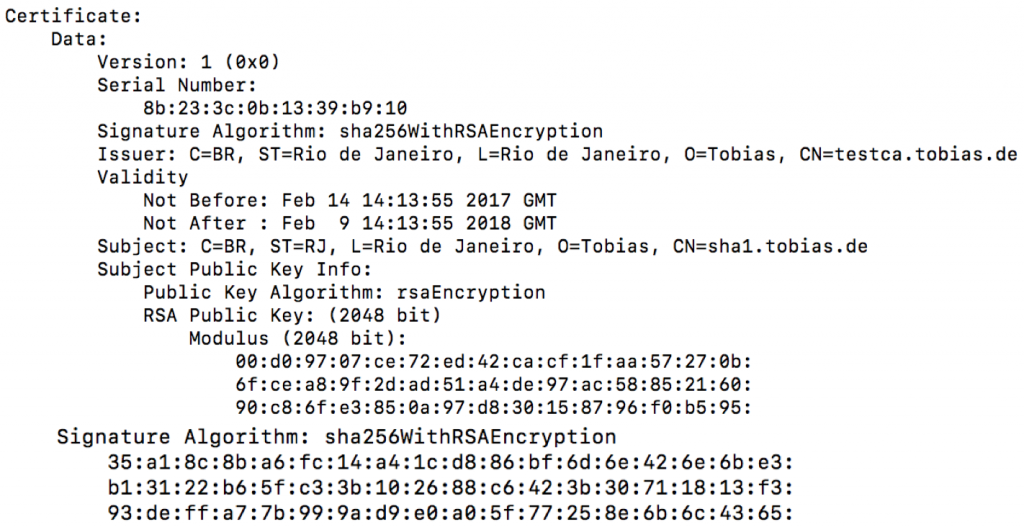
Check signed certificate
openssl x509 -text -noout -in sha1.crt
The certificate`s signature algorithm is using SHA-256. The original CSR`s signature algorithm was SHA-1, but the resulting algorithm is now SHA-256. Even when you cannot change to SHA-256 during CSR creation, or the CSR is only available in SHA-1, it is still possible to change the SHA-256 during the signing process of the CA.
0 Comments