Setup OpenVPN client on Raspberry Pi
OpenVPN uses certificates to authenticate the server and clients. Therefore, the client needs to have a valid client certificate. This certificate needs to be issued by the CA server that also issued the certificate of the OpenVPN server. In my case, this server is installed together with the OpenVPN server on the AWS EC2 instance. The process to create the client certificate is the same as with the server certificate, only the certificate type must be client, or: TLS Web Client Authentication. This is done by specifying the client parameter in the generate certificate request command.
Depending whether or not easy-rsa or any other tool to generate a certificate request is available on the client, the request can be generated directly on the client. The vantage by creating the request on the client is that the private key will stay on the client. In my example, I’ll make use of the already available infrastructure on the OpenVPN server and generate the client request and certificate on the server and copy later the generated artifacts over to the client.
Create client certificate
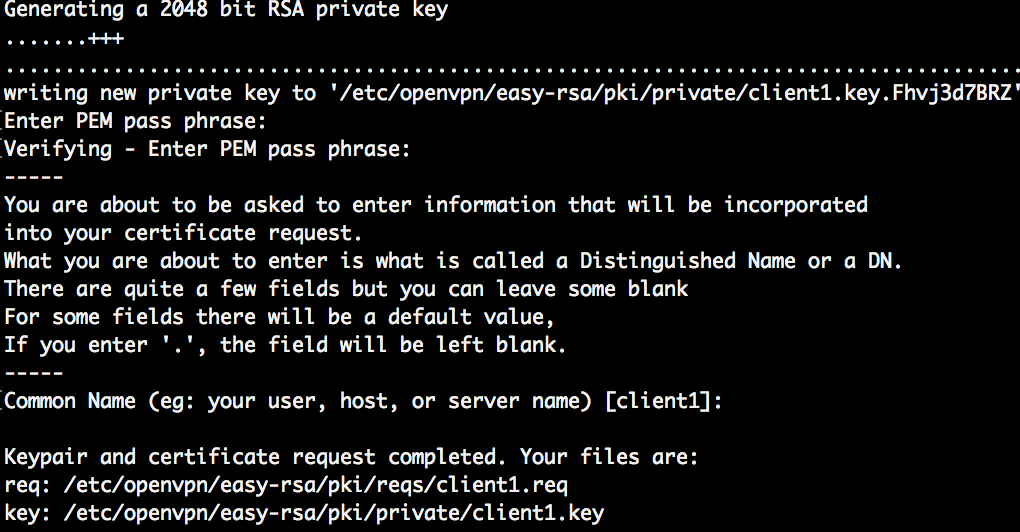
Log in to the CA (OpenVPN) server and issue a client certificate request. The name of the client will be client1. Note that you can use a different name, like the FQDN of the client.
cd /etc/openvpn/easyrsa sudo ./easyrsa gen-req client1
As with the server certificate, give a passphrase and common name.
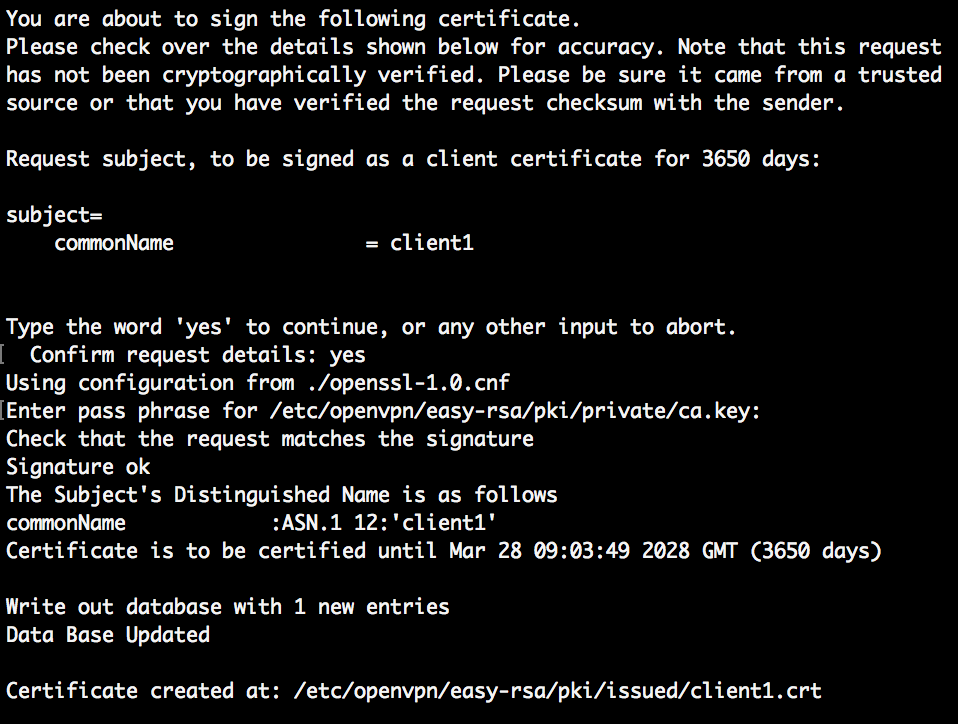
Next: sign the client1 certificate by the CA.
sudo ./easyrsa sign-req client client1
You need to confirm the signing request by entering yes and informing the pass phrase of the CA certificate.
The client certificate is now issued.
- Private key: easy-rsa/pki/private/client1.key
- Public certificate: easy-rsa/pki/issued/client1.crt
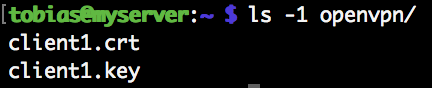
Move these files to the OpenVPN client.
OpenVPN client Installation
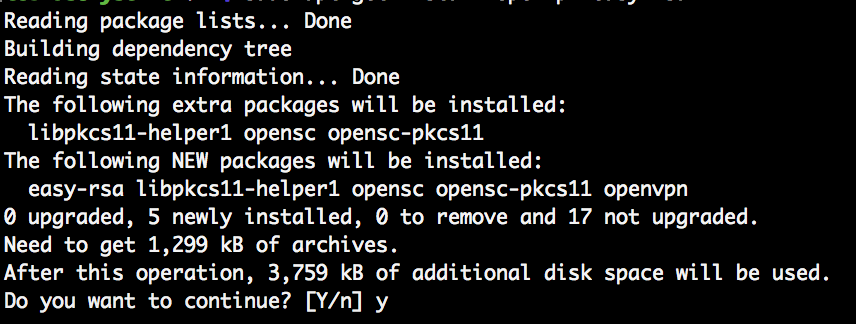
The client going to connect to the OpenVPN server running on AWS EC2 is a Raspberry Pi. The RP uses a Debian based Linux, therefore apt is used to install software. On the RP, install OpenVPN. Easy-rsa is not needed, as the CA is running on the EC2 instance.
sudo apt-get update sudo apt-get install openvpn
Client Certificates
Create a openvpn directory. Can be in /etc/ or in your user’s home. Put the client’s public certificate and privte key there. To use HMCA for additional security, copy the ta.key file from the server there too.
Configuration
Copy the OpenVPN sample client configuration to your openvpn directory and edit the file client.conf.
cd openvpn cp /usr/share/doc/openvpn/examples/sample-config-files/client.conf .
Adjust the following lines to point to the correct server (AWS EC2) and local certificates and key. Example:
- remote server.domain.com 1194
- ca /home/tobias/openvpn/ca.crt
- cert /home/tzobias/openvpn/client.crt
- key /home/tobias/openvpn/client.key
- tls-auth /home/tobias/openvpn/ta.key 1
The tls-auth parameter is needed in case the server is configured to use HCMA. The shared key ta.key from the server is needed for this to work.
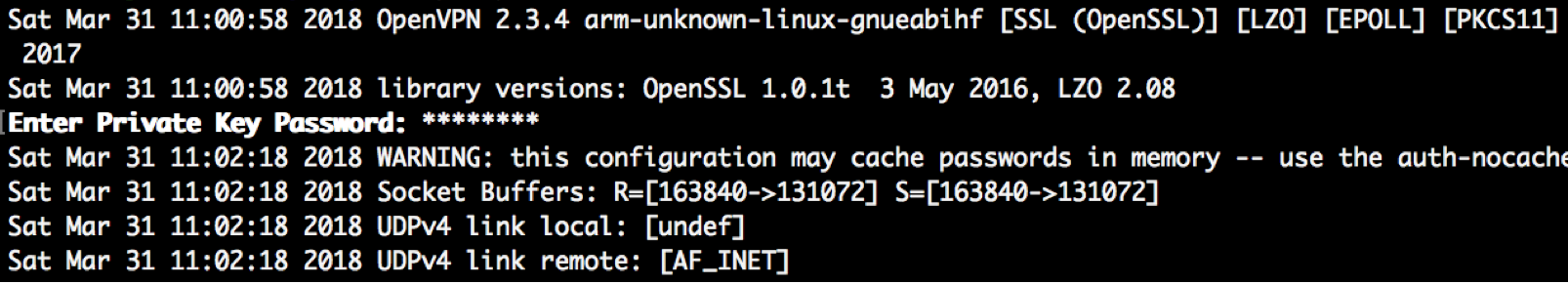
Start OpenVPN client
To start the OpenVPN as client, run the executable and pass the path to the configuration file as parameter.
openvpn ./client.conf
You need to provide the pass phrase of the client1 private key.
The client will automatically connect to the OpenVPN server defined in the client.conf file (remote parameter) and the given port (1194). Make sure that on AWS EC2, this port is accessible for the client.
Result
If all works, the client connects to the server and gets an internal IP assigned.
8 Comments
Jan Viel · March 15, 2020 at 16:39
Hallo,
I have installed OpenVPN Server in a Raspberry pi 3. It works fine.
I made for the second Raspberry pi 3 a client-name and password.
But I have a problem. How do I setup openvpn-client on the second raspberry pi 3.
Can you help me with a step-to-step manual ?
I.m living in the Netherlands, 73 years old and my English is not very good.
Regards
Jan Viel
Tobias Hofmann · March 16, 2020 at 13:50
Hi Jan,
see the section “OpenVPN client Installation” for how to install the OpenVPN client. The steps outlined here will show you how to install the client, configure and copy the certificates and then start the client.
Eric E. Andersen · May 25, 2020 at 04:34
Using PiVPN, I am able to add a user with the terminal command “pivpn -a” which creates a user and a password and a configuration file named (in this case for user “pi”): pi.ovpn. In other OpenVPN front ends, I can import the .ovpn file which eliminates the need to do certificate and key work that you describe. Are you aware of a front end for OpenVPN in Raspbian that would do that?
Thanks!
Alex Buznik · September 8, 2021 at 09:20
Hey Eric. Did you manage to use .ovpn file on raspberry?
Ron · July 10, 2020 at 05:21
I have Raspberry Pi’s on mountain tops around the west coast that we are using for Ham Radio. We have the connected to the internet via cell hotspots. In order to SSH or SCP., we must have a static IP. Our VPN provider will be discontinuing the Static IP servers and replacing them with Dynamic IP servers. This will leave us with no way to connect.
I was thinking of using my Godaddy VPS and getting some static IP’s assigned to it. It is running Centos 7 for the OS. Installing openVPN server on it and openVPN client on the Raspberry’s. Then use my own VPN server. I guess I would need to have some kind of router on the server to know what Raspberry gets what packets.
I am lost…
david · August 28, 2020 at 10:53
Hi there,
Could you cover client keys revoke procedure as well?
Just relived there is no revoke-all script in raspbian openvpn distribution.
Matt · September 22, 2021 at 15:04
Need the client to use a username and password, not a certificate.
Brion · February 25, 2022 at 03:35
Hello, is there a version for Windows 10?