SAP Gateway – Activate and test SAML 2.0 Logon with SAP WebGui for HTML
After establishing the trust between the SAML 2.0 IdP and SP and activating the IdP in SAP Gateway, the ABAP system is configured for SAML 2.0 logons. An easy way to test if SAML 2.0 is working is to log on to SAP WebGui for HTML. This is a standard service delivered always. Therefore, it is also available for NPL.
The default logon procedure for ICF is to check if SAML 2.0 is enabled and then use SAML 2.0. Remember that this means that after activating the trusted SAML 2.0 IdP in transaction SAML2, the default logon method changed: your users are now seeing the SAML 2.0 logon screen.
More information on logon procedures:
SAP Help: Maintaining Logon Procedures
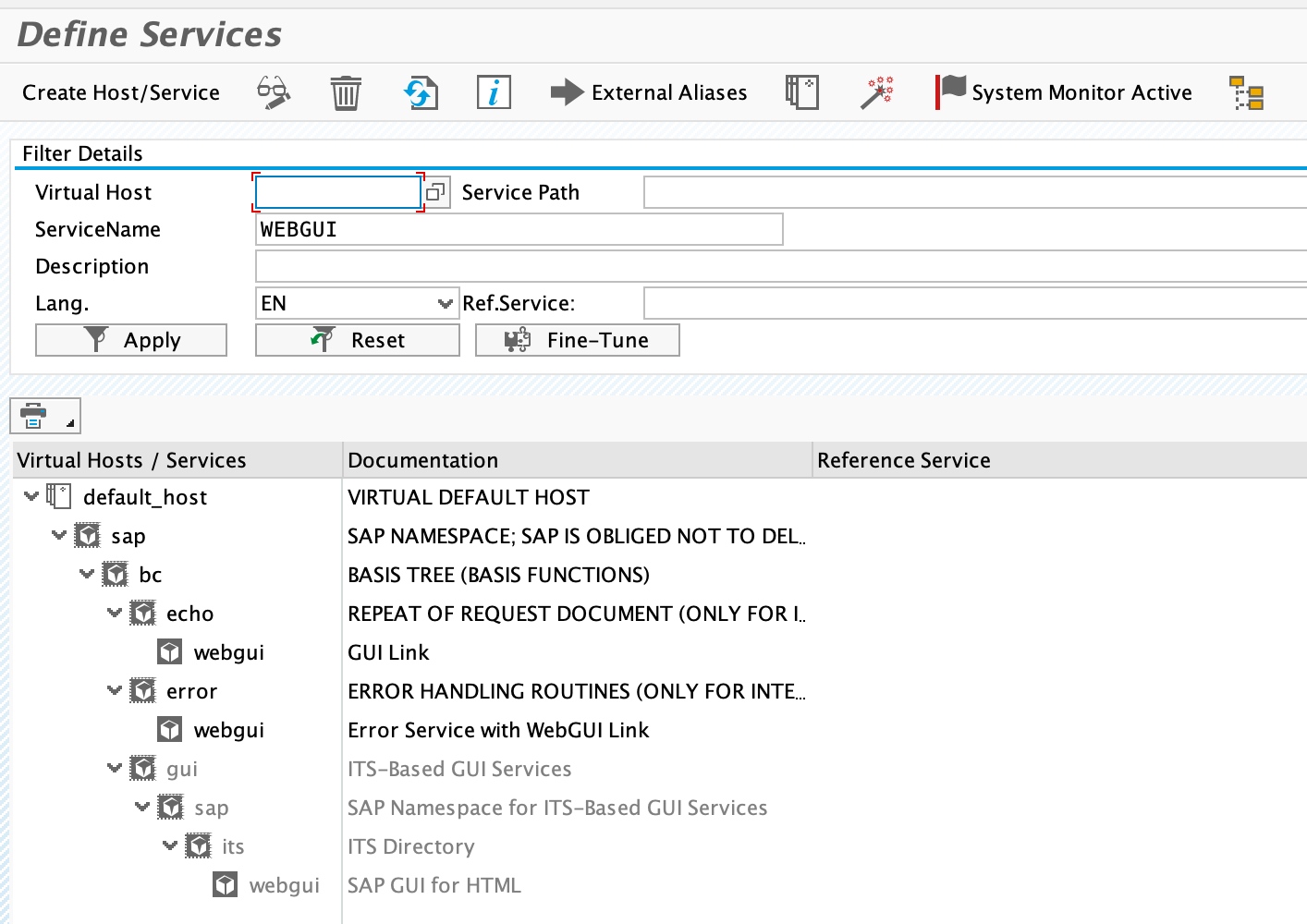
Activate WebGui
In case WebGui is not already activated, activate it.
Tx: SICF Service: /sap/bc/gui/sap/its/webgui
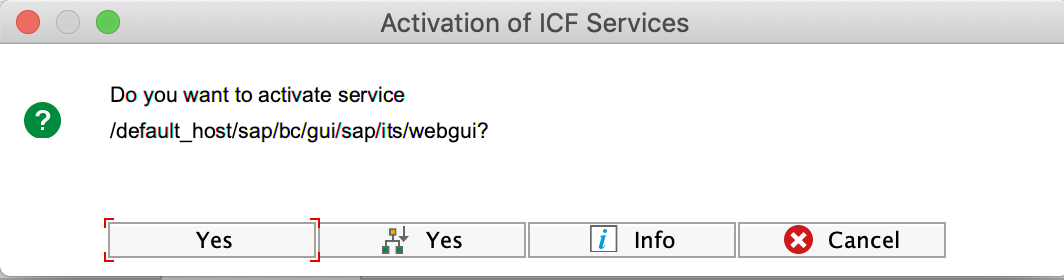
Activate service
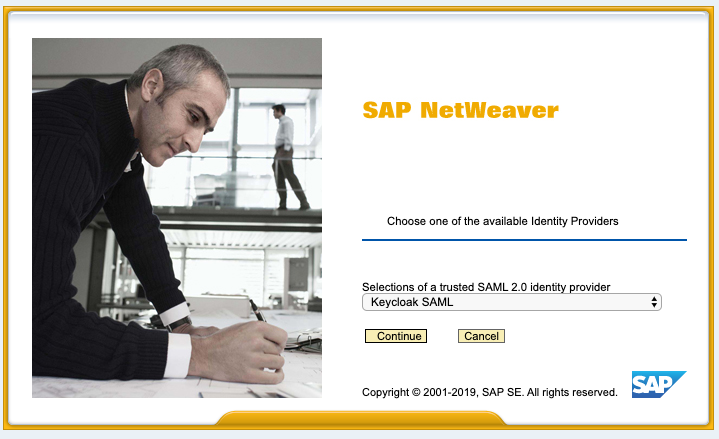
Call service: http://vhcalnplci:8000/sap/bc/gui/sap/its/webgui?sap-client=001&sap-language=EN
You should see the NetWeaver logon screen and the option to select the SAML 2.0 IdP.
Click on Continue will start the SAML 2.0 authentication flow.
http://localhost:8080/auth/realms/SAML/protocol/saml?SAMLRequest=fZHNasMwEIRfxeiuSHJC7C6xITQUDGkITemhN2FviECWXK3cn7ev7NDSHtrrsPPNjLQh3dsBtmO8uAd8GZFi1uwqdpKllHlRFFyuijVX2GleLsuOF2vsuqXOV2uVs%2BwJAxnvKpYvJMsaohEbR1G7mCSpbrhSPFePagXLHFTxzLJdSjBOx9l1iXEAIaxvtb14ilCmWKFTGRFQ257EaXu%2FF0Pw0bfeiqksy%2B58aHFuXLGztoRT8lETmVf8Vt576wjmdRUbgwOvyRA43SNBbGECQ2oNX3BWb6ZrmEeEH%2F7%2F7SkWw7SG1YfjXkq1ET8wV%2BYAh%2BRrdkdvTfsx9e91%2FBurFmpWTMfP8ymMjgZszdlgx7Kttf7tNr1PTGtjGJGJ%2Bhr6%2Bx%2FrTw%3D%3D&RelayState=oucqyqqsxxxoquxworedaoytydoxweddtasuwrs&SigAlg=http%3A%2F%2Fwww.w3.org%2F2000%2F09%2Fxmldsig%23rsa-sha1&Signature=Qt%2BXguQo9LJzBBM%2BjsE%2F7Dut7%2FPk38AEqzmHHTlGfy2s9uOXni%2BhZU7cEFENgSQ1NXCvoJy3kTXQTO0%2BhPNQ%2FKy%2Bo8Ht%2BIxDXgKHgeaq2mvTwPVDuJ0lOQnaOKCYam0N0sMCBKkjZQk7686lCw0bYdmdX5lvkYXUXpKM1C941stioA8mk5kvYlR8xQwHw%2B1E138GRxmJIW1qUvR2Nu42%2FY%2BnVvrSmAlHn9faXEk9fdXYdLdf4%2Fy6G1A5qmY89il0VatEZzjBJ3mYlLtmuTln86QVnTy33ejjGGbHT05aWIz4NrXzpVBjDUgzdvD3mP3PgjOayDv78Wsed3iYmgQIKA%3D%3D
Keycloak is called. Note the realm SAML: auth/realms/SAML/protocol/saml
A SAMLRequest is added to the URL, as the IdP is configured for HTTP Redirect.
SAMLRequest=fZHNasMwEIRfxeiuSHJC7C6xITQUDGkITemhN2FviECWXK3cn7ev7NDSHtrrsPPNjLQh3dsBtmO8uAd8GZFi1uwqdpKllHlRFFyuijVX2GleLsuOF2vsuqXOV2uVs%2BwJAxnvKpYvJMsaohEbR1G7mCSpbrhSPFePagXLHFTxzLJdSjBOx9l1iXEAIaxvtb14ilCmWKFTGRFQ257EaXu%2FF0Pw0bfeiqksy%2B58aHFuXLGztoRT8lETmVf8Vt576wjmdRUbgwOvyRA43SNBbGECQ2oNX3BWb6ZrmEeEH%2F7%2F7SkWw7SG1YfjXkq1ET8wV%2BYAh%2BRrdkdvTfsx9e91%2FBurFmpWTMfP8ymMjgZszdlgx7Kttf7tNr1PTGtjGJGJ%2Bhr6%2Bx%2FrTw%3D%3D
The Redirect payload can be decoded.
<samlp:AuthnRequest ID="S08002777-0476-1eda-838d-76edd3a24612" Version="2.0" IssueInstant="2019-11-21T14:32:17Z" Destination="http://localhost:8080/auth/realms/SAML/protocol/saml" ForceAuthn="false" IsPassive="false" xmlns:samlp="urn:oasis:names:tc:SAML:2.0:protocol"><saml:Issuer xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion">NPL001</saml:Issuer><samlp:NameIDPolicy Format="urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified" AllowCreate="true"/></samlp:AuthnRequest>
The Keycloak logon page is shown.
Log in to Keycloak with your Keycloak username and password. The username must exist in the SAP system, as this is how the NameID property was configured.
Login.
Result
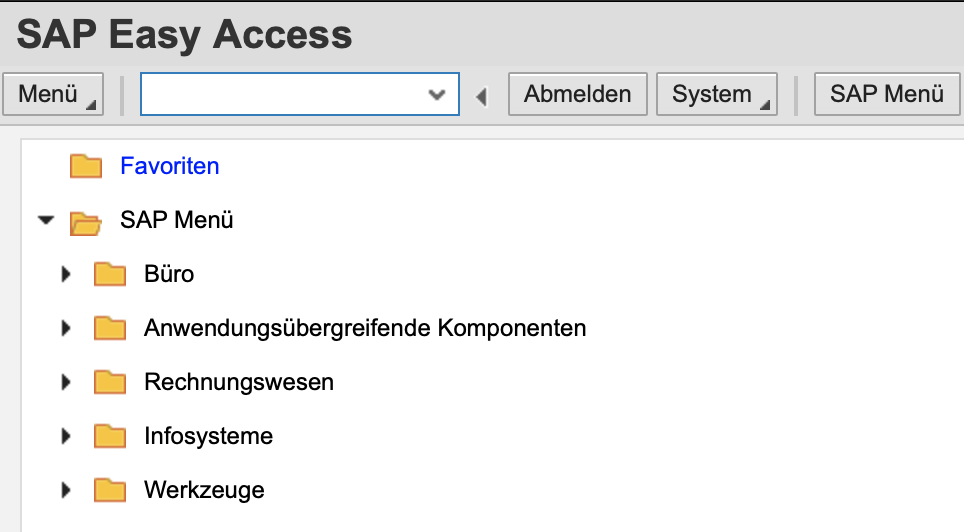
SAP WebGui for HTML opens.
Logon via SAML 2.0 works!
2 Comments
widalvep · January 22, 2022 at 08:02
The same X.509 client certificates can be used for Web SSO also to SAP and non-SAP systems if they do not support SAML 2.0 yet. This scenario could be implemented also with SAML 2.0 identity providers from other vendors because SAP Secure Login Server capabilities include integration with different identity providers. However, we recommend the SAP IDP because of the competitive advantages the SAP product offers.
Create user in NetWeaver via SAML 2.0 – 4 – Configure SAML 2.0 Identity Provider | It's full of stars! · September 18, 2020 at 10:31
[…] user creation scenario is an extension to the “simple” SAML 2.0 SSO scenario. Therefore, a pre-requisite is to have the SAML 2.0 IdP and SP configured to trust each other. A […]