Troubleshooting – OAuth 2.0 NW ABAP token service return HTTP 500 Internal Server Error
Problem
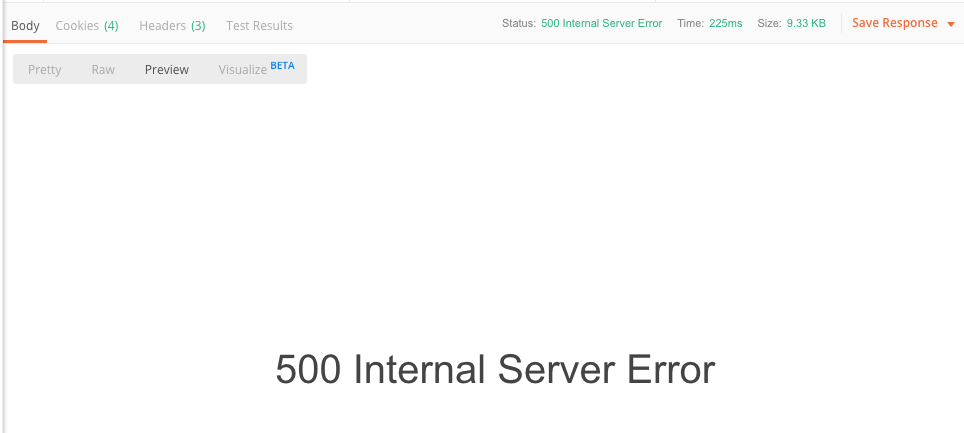
After sending a request to the access token endpoint /sap/bc/sec/oauth2/token you get an internal server error 500.
Investigation
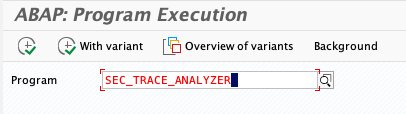
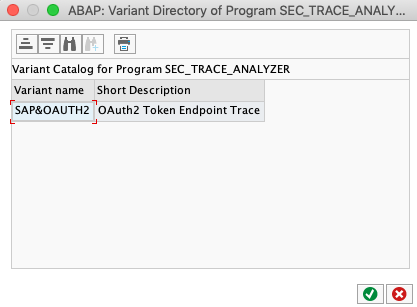
Tx: SA38 Program: SEC_TRACE_ANALYZER
Run program.
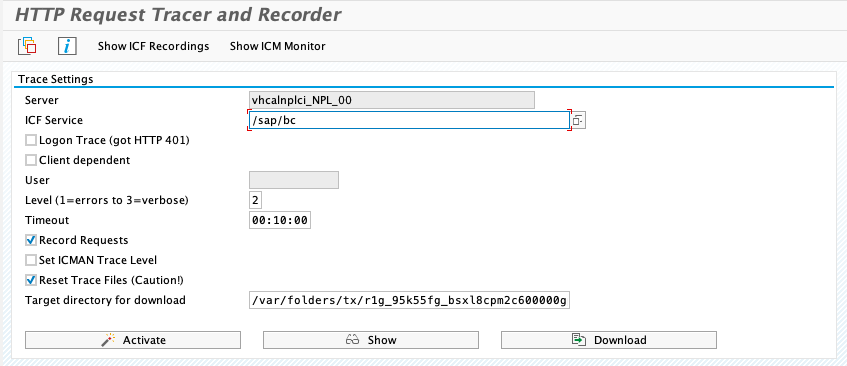
Select OAuth varian: click on Get Variants
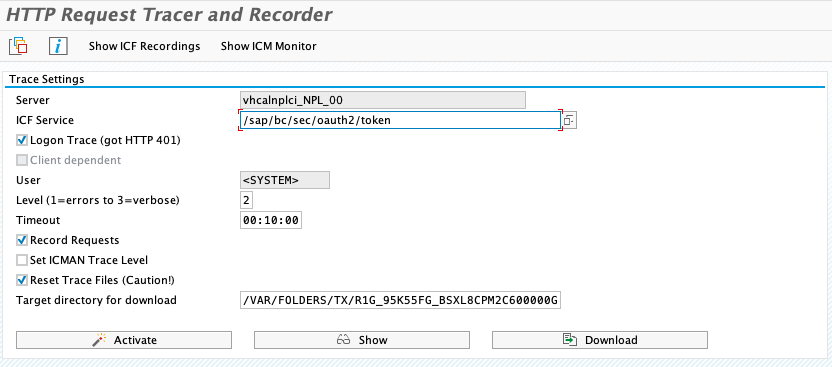
Click on Activate
Trace is active.
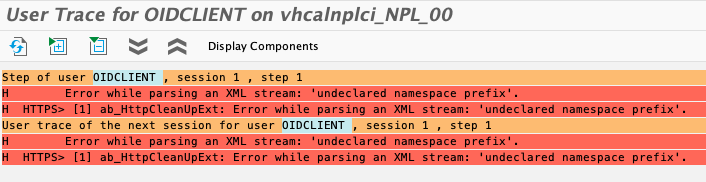
Reproduce the issue. The log trace for the user will show the cause of the error:
Error while parsing an XML stream: undeclared namespace prefix.
Root cause
The XML send by the IdP in the SAMLResponse parameter is invalid. A sample assertion to send by the IdP can be found in SAP Help. In my case, Keycloak returned:
<samlp:Response xmlns:samlp=”urn:oasis:names:tc:SAML:2.0:protocol” xmlns:saml=”urn:oasis:names:tc:SAML:2.0:assertion” Destination=”https://vhcalnplci:44300/sap/saml2/sp/acs/001″ ID=”ID_7716c053-3127-4569-ba8b-0b8ac71b5b46″ InResponseTo=”S08002777-0476-1eda-81c0-9be5c3b6e0d8″ IssueInstant=”2019-11-13T14:21:21.799Z” Version=”2.0″><saml:Issuer>http://localhost:8080/auth/realms/master</saml:Issuer>
[…]<samlp:Status><samlp:StatusCode Value=”urn:oasis:names:tc:SAML:2.0:status:Success”/></samlp:Status>
<saml:Assertion xmlns=”urn:oasis:names:tc:SAML:2.0:assertion” ID=”ID_f9bce362-950a-4845-a962-338861b8586d” IssueInstant=”2019-11-13T14:21:21.798Z” Version=”2.0″><saml:Issuer>http://localhost:8080/auth/realms/master</saml:Issuer><saml:Subject><saml:NameID Format=”urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified”>oidclient</saml:NameID>[…]<saml:Attribute Name=”Role” NameFormat=”urn:oasis:names:tc:SAML:2.0:attrname-format:basic”></saml:Assertion></samlp:Response>
The SAML assertions are in the namespace xmlns:saml. This namespace must be passed with the Assertion to Gateway. If not, the XML is invalid. When sending the SAMLResponse to the OAuth toke issuer service from SAP NetWeaver ABAP, make sure that the XML file is valid.
A valid XML for the above example looks like:
<?xml version=’1.0′ encoding=’UTF-8′?>
<saml:Assertion xmlns:saml=”urn:oasis:names:tc:SAML:2.0:assertion” ID=”ID_f9bce362-950a-4845-a962-338861b8586d” IssueInstant=”2019-11-13T14:21:21.798Z” Version=”2.0″><saml:Issuer>http://localhost:8080/auth/realms/master</saml:Issuer><saml:Subject><saml:NameID Format=”urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified”>oidclient</saml:NameID>[…]</saml:AttributeStatement>
</saml:Assertion>
What Keycloak delivers is:
<saml:Assertion xmlns="urn:oasis:names:tc:SAML:2.0:assertion"
What is needed is:
<saml:Assertion xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion"
Solution
The “:saml” part is missing in xmlns. As you are only going to send the assertion to NW, include the saml namespace: xmlns:saml.
0 Comments